Introduction
XSStrike is a Cross Site Scripting detection suite equipped with four hand written parsers, an intelligent payload generator, a powerful fuzzing engine and an incredibly fast crawler.
The Most Advanced XSS Detection Suite: XSStrike
Instead of injecting payloads like other tools, XSStrike uses multiple handmade parsers to analyse the web application’s response. After analyse, it crafts payloads that are guaranteed to work with context analysis integrated with a fuzzing engine.
It can also crawl, fingerprint and fuzz WAFss. In addition, it can scan for DOM XSS vulnerabilities. XSStrike is fully compatible with Python 3.4+.Features:
- Reflected and DOM XSS Scanning
- Multi-threaded crawling
- Context analysis
- Configurable Core
- Highly Researched Work-flow
- WAF detection & evasion, WAF Fingerprinting
- Handmade HTML & JavaScript parser
- Powerful fuzzing engine
- Intelligent payload generator
- Complete HTTP Support
- Powered by Photon, Zetanize and Arjun
- Well documented code and regular updates
Supported OSs:
- Linux (Arch, Debian, Ubnutu), Termux, Windows (7 & 10), MacOSX.
Mac & Windows don’t support ANSI escape sequences so the output won’t be colored on Mac & Windows.
Requirements:
tld,requests,fuzzywuzzy
Install
First you’ll need to clone it from the git repo:$ git clone https://github.com/s0md3v/XSStrike.gitThen naviagate to XSStrike directory and install the requirements:
$ cd XSStrike $ pip install -r requirements.txtTo run XSStrike:
$ python xsstrike
Usage
To list all available arguments, type--help:usage: xsstrike.py [-h] [-u TARGET] [--data DATA] [-t THREADS]
[--fuzzer] [--update] [--timeout] [--params] [--crawl]
[--skip-poc] [--skip-dom] [--headers] [-d DELAY]
optional arguments:
-h, --help show this help message and exit
-u, --url target url
--data post data
-t, --threads number of threads
-l, --level level of crawling
--fuzzer fuzzer
--update update
--timeout timeout
--params find params
--crawl crawl
--skip-poc skip poc generation
--skip-dom skip dom checking
--headers add headers
-d, --delay delay between requests
Scan a single URL example
- Option:
-uor--url
$ python xsstrike.py -u "http://example.com/search.php?q=query"Supplying POST data:
$ python xsstrike.py -u "http://example.com/search.php" --data "q=query"
Crawling example
- Option:
--crawl
$ python xsstrike.py -u "http://example.com/page.php" --crawlFinding hidden parameters:
- Option:
--params
$ python xsstrike.py -u "http://example.com/page.php" --params
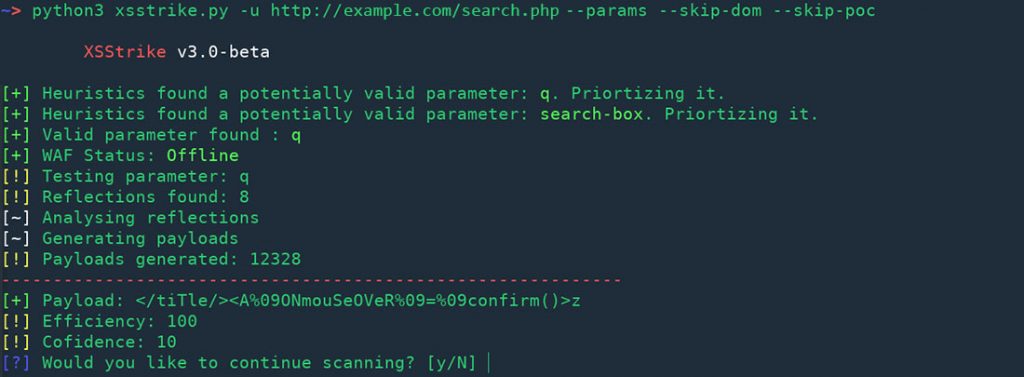
Skip POC Generation
- Option:
--skip-poc
$ python xsstrike.py -u "http://example.com/search.php?q=query" --skip-poc
Skip DOM Scanning
- Option:
--skip-dom
$ python xsstrike.py -u "http://example.com/search.php?q=query" --skip-domFor detailed documentation and additional examples, clic the “documentation” button below.
Source: https://www.cyberpunk.rs/advanced-xss-detection-suite-xsstrike



إرسال تعليق
Komentar Spam Akan kami Hapus